Perimeter penetration testing
 And depending on when you had your last perimeter pen test, you may not know about them for quite some time. The objective of web application penetration testing is to identify security issues resulting from insecure development practices in the design, coding and publishing of software. You will have 90 days from the end of your lab time to schedule and take this most unique and challenging of ethical hacking certification exams. The webinar will take place on 1 November , from 3: How penetration testing can help prevent the most common types of attack; The differences between a penetration test and a vulnerability assessment; Why penetration tests are vital to uncovering vulnerabilities before criminals do; and How to conduct a penetration testing programme. A penetration test may be limited to specific network areas or allow the tester full network access to most accurately simulate an attacker. A perimeter penetration test is designed to look simply at the systems that you have facing the internet.
And depending on when you had your last perimeter pen test, you may not know about them for quite some time. The objective of web application penetration testing is to identify security issues resulting from insecure development practices in the design, coding and publishing of software. You will have 90 days from the end of your lab time to schedule and take this most unique and challenging of ethical hacking certification exams. The webinar will take place on 1 November , from 3: How penetration testing can help prevent the most common types of attack; The differences between a penetration test and a vulnerability assessment; Why penetration tests are vital to uncovering vulnerabilities before criminals do; and How to conduct a penetration testing programme. A penetration test may be limited to specific network areas or allow the tester full network access to most accurately simulate an attacker. A perimeter penetration test is designed to look simply at the systems that you have facing the internet.






Cracking the Perimeter (CTP)
 They mimic hackers whose incentive is to steal your information, to alter it in their favour, or prevent you accessing it. Learn more about Intruder here. Network and Application Testing. Fixing these may prevent unwanted disturbances. As you progress through the CTP course materials, you will practice the tools and techniques directly on various targets in our online labs. Our clients tell us that we're the best pen-testing firm they've worked with.
They mimic hackers whose incentive is to steal your information, to alter it in their favour, or prevent you accessing it. Learn more about Intruder here. Network and Application Testing. Fixing these may prevent unwanted disturbances. As you progress through the CTP course materials, you will practice the tools and techniques directly on various targets in our online labs. Our clients tell us that we're the best pen-testing firm they've worked with.

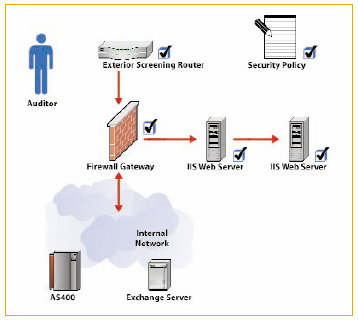
Network & Application Testing | Penetration Testing | Security Intelligence
London Conference Cyber Resilience Week Another great event for Cyber Resilience Week! Perimeter - A perimeter penetration test probes the security of the network perimeter and externally accessible devices and attempts to gain access to corporate assets from outside the organization. Executive report, which is an easy to follow 4 page report that includes information about the penetration test, list of the findings and a short explanation of the security fixes or mitigation techniques Technical report, which includes the following sections: However, just like real attackers, we do not limit ourselves to particular rigid methodologies.



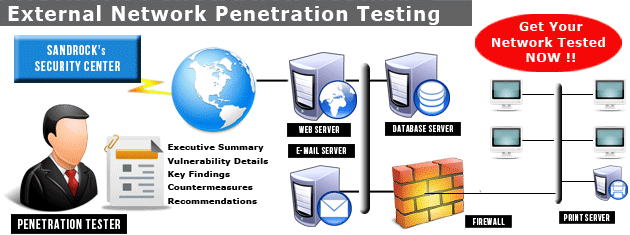
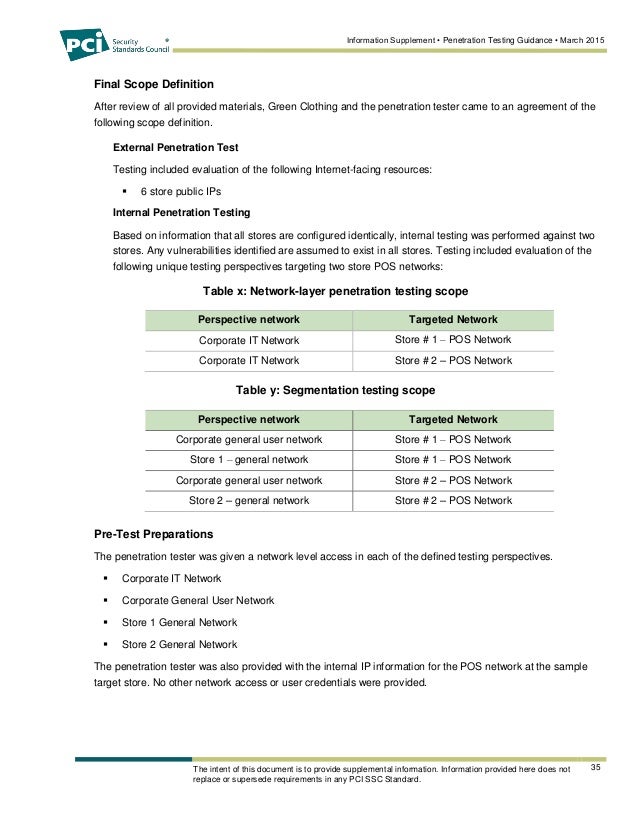

What Is Penetration Testing? – Part One: The Perimeter

Description: This reduces the scope of PCI requirements needed to be compliant. Depending what type of scenario you are worried about, you may want to know the differences before you decide which type of penetration testing to perform. A few questions to consider: Executive report, which is an easy to follow 4 page report that includes information about the penetration test, list of the findings and a short explanation of the security fixes or mitigation techniques Technical report, which includes the following sections:
Views: 5409
Date: 04.02.2016
Favorited: 5











.jpg)























User Comments
Post a comment
Comment: