Penetration test definition
 However, software systems have many possible input streams, such as cookie and session data, the uploaded file stream, RPC channels, or memory. Minimal security breach potential ensures system reliability. Many other specialized operating systems facilitate penetration testing—each more or less dedicated to a specific field of penetration testing. You have exceeded the maximum character limit. Predictive analysis for business requires the right data More data doesn't always benefit predictive analytics projects. At the Spring Joint Computer Conference, many leading computer specialists again met to discuss system security concerns. The fundamental purpose of penetration testing is to measure the feasibility of systems or end-user compromise and evaluate any related consequences such incidents may have on the involved resources or operations.
However, software systems have many possible input streams, such as cookie and session data, the uploaded file stream, RPC channels, or memory. Minimal security breach potential ensures system reliability. Many other specialized operating systems facilitate penetration testing—each more or less dedicated to a specific field of penetration testing. You have exceeded the maximum character limit. Predictive analysis for business requires the right data More data doesn't always benefit predictive analytics projects. At the Spring Joint Computer Conference, many leading computer specialists again met to discuss system security concerns. The fundamental purpose of penetration testing is to measure the feasibility of systems or end-user compromise and evaluate any related consequences such incidents may have on the involved resources or operations..gif)

Yana. Age: 29. I have lots of erotic toys, as well many hot outfits (from elegant dresses to leather/latex outfits, stockings, high heel shoes and boots) and i'm willing to play... So... I'm sure that the the time you'll have with me will leave you the feeling of a precious moment spent in the company of a generous, soft, harmonious and passionate lady and will definately be something to remember because i love being the perfect experience for everyone.



Penetration Testing Experts
 By submitting you agree to receive email from TechTarget and its partners. Security issues uncovered through the penetration test are presented to the system's owner. How do you test self-driving car technology when the consequences of an error can be fatal? Please help improve this section by adding citations to reliable sources. What Is Penetration Testing? Demonstrates a good-faith effort to protect customer information Pen-testing tools include: How does Penetration Testing work?
By submitting you agree to receive email from TechTarget and its partners. Security issues uncovered through the penetration test are presented to the system's owner. How do you test self-driving car technology when the consequences of an error can be fatal? Please help improve this section by adding citations to reliable sources. What Is Penetration Testing? Demonstrates a good-faith effort to protect customer information Pen-testing tools include: How does Penetration Testing work?



Georgia. Age: 20. hi, i am desdemona, a hot brunete from bucharest/romania -i would love you to contact me by phone directly - i check emails hardly -
Penetration Testing for IT Infrastructure | Core Security
Penetration Testing Made Easy. With LinuxKit, Docker continues its push for better container portability. A few are vulnerable to SQL injections on certain strings. The goal of penetration testing is to determine if unauthorized access to key systems and files can be achieved.
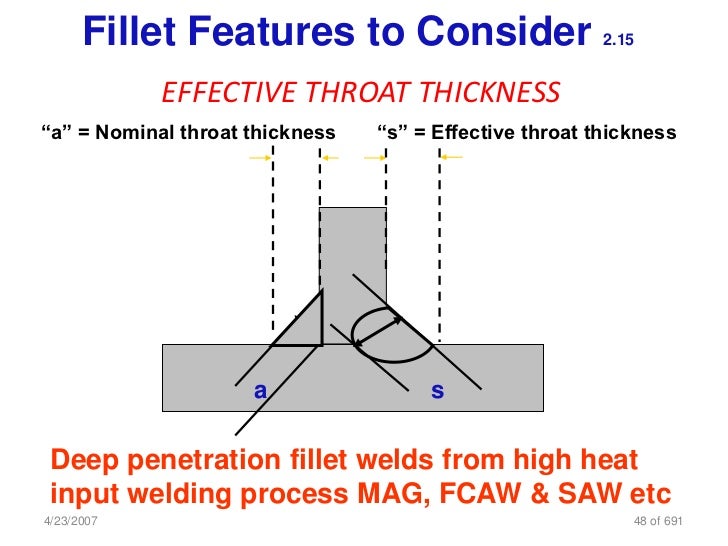



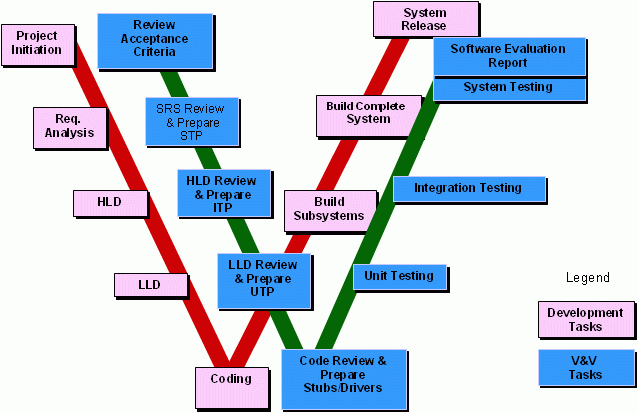
Penetration Testing, The Real Definition
Description: From Wikipedia, the free encyclopedia. By continuing to use our site [without first changing your browser setting], you consent to our use of cookies. Front-end microservices offer flexibility for developers Looking to create a stronger and more transparent relationship between front-end and back-end components? We offer many wireless penetration services involving security tests of standard corporate Wi-Fi networks to assessments of specialized wireless solutions.
Views: 1420
Date: 21.07.2016
Favorited: 5
































User Comments
Post a comment
Comment: